You know the basics already, now we will go for a more complex problem.
We all know about the dangers of hacking and how critical it is to secure our applications, especially those facing the internet.
What is the best way to make sure we have a robust infrastructure as well as a very secure one ?
Say, we need to have a heavy load web server on port 443 (secure HTTP or HTTPS) and a mail server. Normally, in the VPS business, we have all the components running on a VPS, the web server as such, the database, PHP, the mail server. We can, of course, have more servers, one with the database, one with the web server and PHP, one with the mail and even one reverse proxy which is reading the web server and caching queries and serving the visitors.
But, there are some problems with this. First, all traffic between these servers will be counted, second, all ports will have to be exposed to the internet, even if we run some iptables rules to allow access only from one IP or the other. There is also the problem of load balancing and increasing capacity fast if needed.
In a real IaaS, it is simple to bypass all these potential problems.
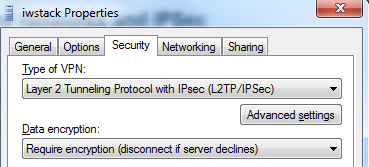
First, we will create an isolated network, something similar with our corporate or home LAN, it will be completely isolated from the internet, we will then allow access only to the ports/IPs we need and we will setup IPsec tunnels to connect with our laptop or even corporate LAN and make the isolated network part of our LAN.
Say we need the following:
1 Database server, 2 Web servers with load balancing, 1 reverse proxy server to cache the requests. They will be arranged like in the diagram:
All that will be open will be port 443 for HTTPS and the only server that will have that port reachable, will be the proxy server, all the others will be inaccessible from the internet.
So, we proceed to create the zone by creating the fist vm, say the database server:
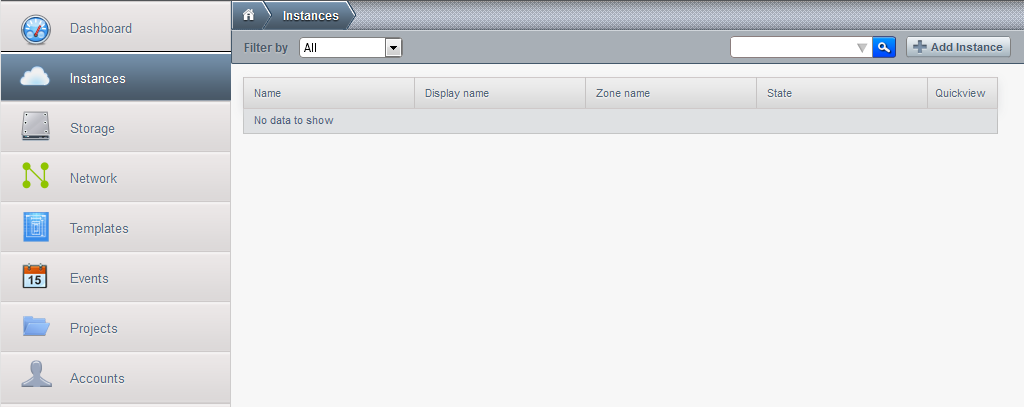
Click add instance. Proceed as in previous tutorials to create an instance with an important exception:
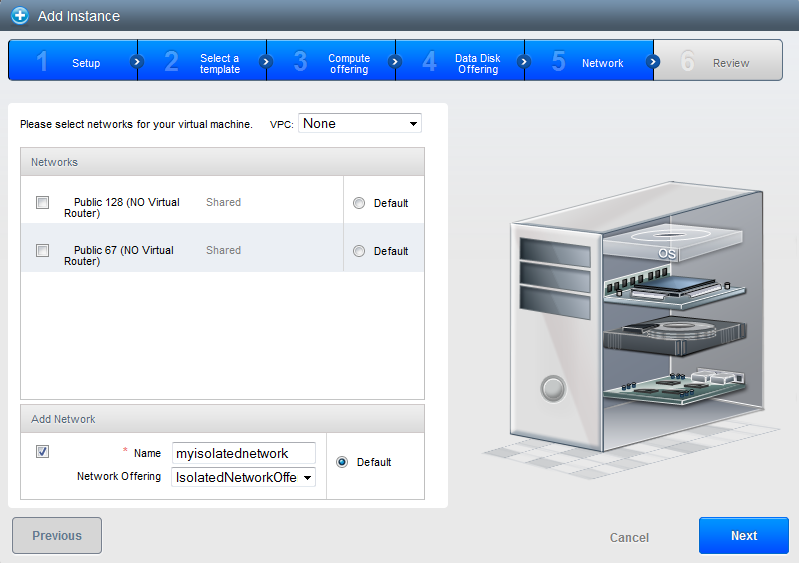
Make sure you do not have any of the shared networks ticked. Then check the box below at Add network and name it. This will create the default isolated network and will also create the automated virtual router VM.
You may wish to add a second disk (DATA DISK) to your server, where you will save the database to keep it separate from the operating system so it is easier to take snapshots and upgrade OS (if you keep all data there, including the logs and access settings among other things) in step 4.
We have now the first VM on the isolated network. However it is really isolated by default, can't even access the internet, we need to allow it to get updates. If you really wish to have it access only the mirror for updates, you can limit it's access to a mirror or two only and one external server if you wish to dump the database there from time to time. But I will allow access to all internet while leaving internet access to the VM completely off as it will host the database and has no business exposing that to the internet.
Go to Network, hover your mouse over the plus near your newly created isolated network and go to View IP addresses arrow:
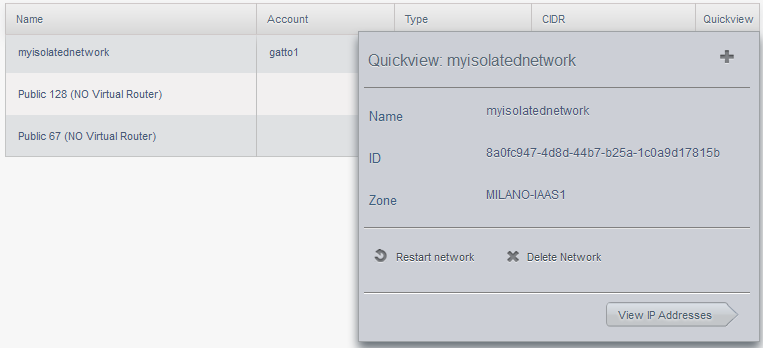
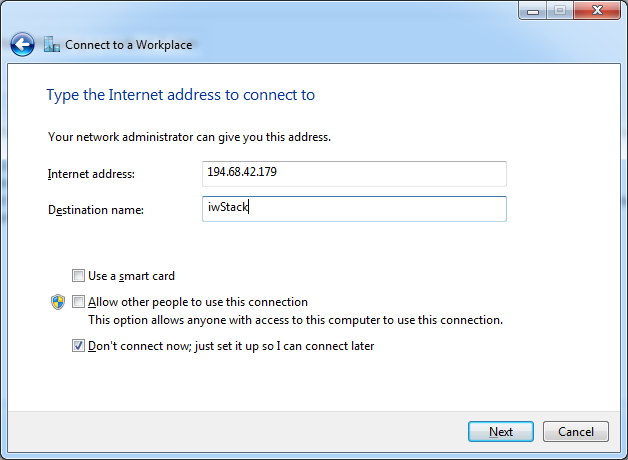
Note your IP address, this will be your external IP, however, your VM has another ip address (you can see it with ipconfig). Remember you will allow internet access based on vm name, not internal IP address as you would do on your local network at home or your corporate LAN. Let's allow this VM to access the internet (you can replace 0.0.0.0/0 network mask with something else if you wish to allow only certain IPs, of course, I will allow the VM to access the whole internet), but first, let's enable VPN access:
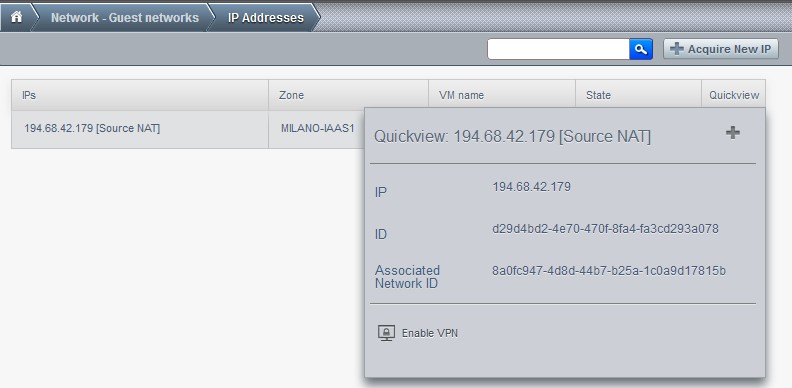
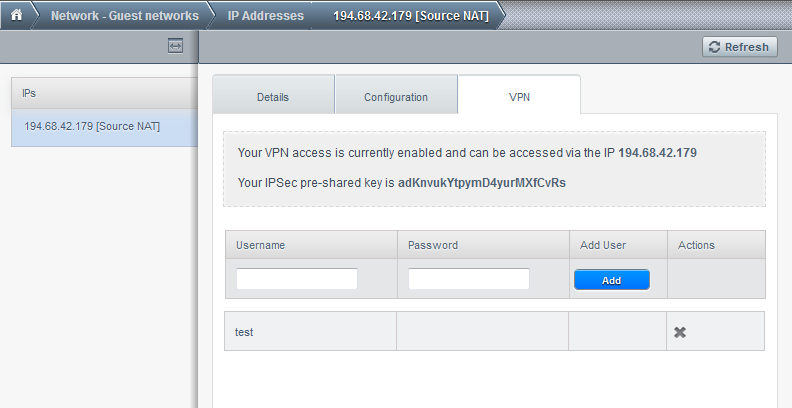
You should also create an user and password in the VPN tab. They will be used to connect to the VPN.
Now, lets allow access to the internet. Click the IP address in the previous screen and you get this in the configuration tab:
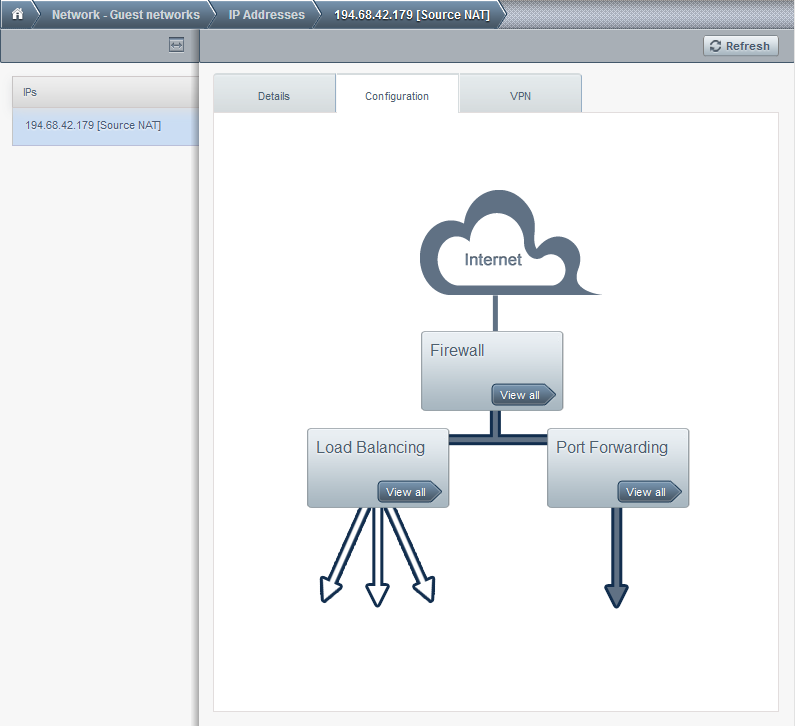
Click on the View all arrow in the firewall section:
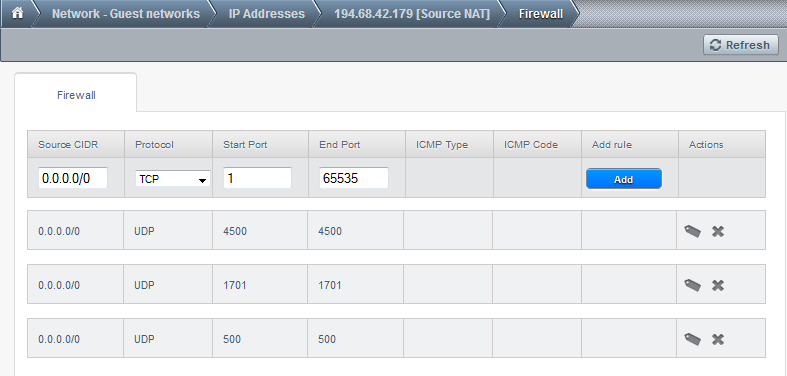
If you are inserting the numbers as in the picture and then do Add, a new rule which allows access to any TCP port on the whole internet will be added. We have no reason to add UDP access, so we wont, but the procedure is similar. Notice there are already some rules there, since we added the VPN access.
For more information about the firewall, please look at the respective tutorial.
Now we can go and update the VM, install the database server, then add the 2 webservers too and the proxy one. They can all access the internet, the settings apply for all current and future VMs in this particular network.